
MOVEit Transfer Exploitation
July 12, 2024
Topics
- MOVEit
- exploit
- vulnerability

July 12, 2024
Topics
A newly disclosed critical security flaw in Progress Software's MOVEit Transfer is already being exploited in the wild shortly after the bug's details were made public. The vulnerability, identified as CVE-2024-5806 with a CVSS score of 9.1, involves an authentication bypass affecting versions 2023.0.0 before 2023.0.11, 2023.1.0 before 2023.1.6, and 2024.0.0 before 2024.0.2.
MOVEit helps your organization meet cybersecurity compliance standards, such as PCI-DSS, HIPAA, GDPR, SOC2, and more, by providing a secure environment for your most sensitive files and ensuring the reliability of core business processes. MOVEit Transfer facilitates the management and control of business-critical file transfers by consolidating them into one system and offers file encryption, security, activity tracking, tamper-evident logging, and centralized access controls. Additionally, it supports compliance with SLAs, internal governance requirements, and regulations like PCI, HIPAA, CCPA/CPRA, and GDPR.
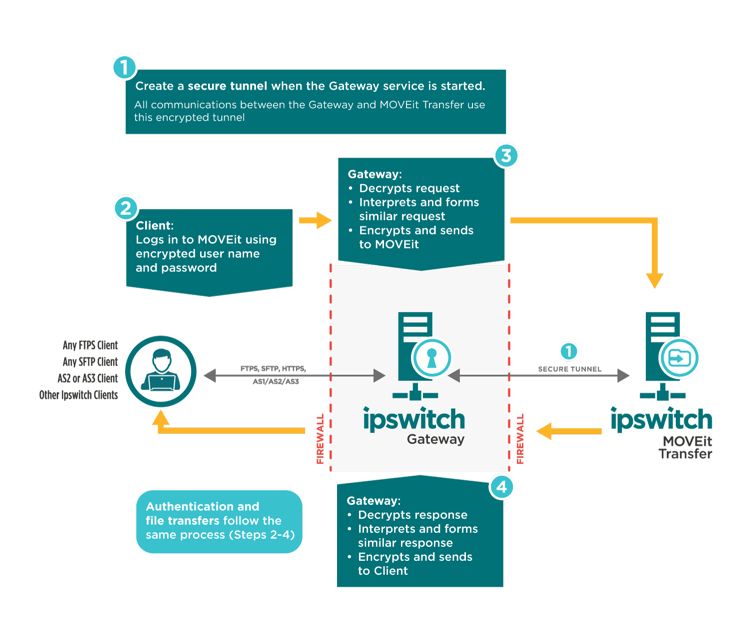
MOVEitGateway version 2024.0.0 has been found to have a bypass vulnerability, CVE-2024-5805, CVSS score: 9.1. Exploiting this flaw allows attackers to bypass SFTP authentication gaining access to MOVEit transfer and Gateway systems. CVE-2024-5806 can impersonate any user on the server that involves both MOVEit and IP Works SSH library.
Rapid7 noted that CVE-2024-5806 exploits need the following requirements, the username, remote authentication capability, and public internet access of SFTP. About 2,700 MOVEit transfers are online and most of them are in the U.S. and Europe.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced that in January, its Chemical Security Assessment Tool (CSAT) was targeted by an unknown threat actor. The attack exploited security vulnerabilities in the Ivanti Connect Secure (ICS) appliance, specifically CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893.

To mitigate risks, Progress Software advises blocking public RDP access and limiting outbound access from MOVEit Transfer servers. Users are also encouraged to apply the security patches published by MOVEit and updating IOCs, as published by CISA. Modify firewall rules to deny HTTP and HTTPs traffic to MOVEit Transfer on ports 80 and 443 until MOVEit has its security patches.
The critical vulnerabilities CVE-2024-5805 and CVE-2024-5806 in Progress Software's MOVEit Transfer, with a CVSS score of 9.1, highlight the urgent need for organizations to update their systems and follow recommended security measures. These flaws allow for severe exploits, including authentication bypass and user impersonation. Adhering to Progress Software's advice to block public RDP access and limit outbound access from MOVEit Transfer servers is crucial to safeguarding sensitive data and maintaining compliance.